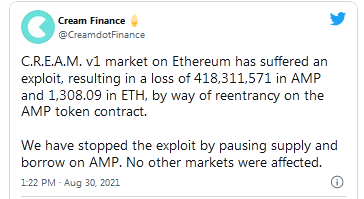
According to Cream Finance, the hack was executed "by way of reentrancy on the AMP token contract."
Cream Finance has reported a major security attack, resulting in a $25 million loss.
Reentrancy Bug Behind Cream Finance Exploit
Cream Finance has been exploited.
The DeFi lending protocol reported its CREAM V1 market had been targeted Monday.
The hacker took advantage of a reentrancy bug on the token contract for AMP, a Consensys-backed digital collateral token listed within the dApp.
The exploit allowed the hacker to steal 41.8 million AMP tokens and 1308.09 ETH, currently worth about $25 million. The supply and borrowing on AMP tokens have been paused.
The hacker executed the hack using a flash loan before exploiting the reentrancy bug. Reentrancy-based vulnerabilities are one of the most common types of security bugs in smart contracts.
Cream Finance is a lending and borrowing protocol that takes inspiration from Compound. It forked the DeFi blue chip and added different asset pools and its own governance token. AMP used the ERC-1820 (based on ERC-777) token standard, which allowed for a reentrancy function.
Smart contract security firm PeckShield, which led the initial analysis, told Crypto Briefing that there might be a “composability risk between Compound-based lending protocols and ERC-777-like tokens.”
PeckShield’s analysis shows that the exploit began when the hacker took out a flash loan of 500 ETH and deposited it as collateral to borrow 19 million AMP tokens. Then, the hacker re-borrowed 355 ETH by leveraging the reentrancy bug. The hacker self-liquidated the loan and repeated the process multiple times to extract funds.
The CREAM token has suffered a relatively minor hit in the fallout, trading down 4.8% at about $167. While both Cream Finance and PeckShield are still investigating the attack, a post-mortem is due to follow soon.
